iPXE & NAC Authentication
Introduction
In this post I’ll be going over how to authenticate with Network Access Control (NAC) using iPXE, this is a follow-up post to my previous posts:
What is NAC?
Network Access Control (NAC) is a security methodology that allows us to restrict or block access to the network based on the identity of the user or device. Traditionally this is handled through Radius authentication at the switch or wireless controller level via 802.1x (EAP) or MAB (MAC Address Bypass), then either blocking the port or providing a Port Based ACL (Access Control List) or VLAN (Virtual Network).
What is MAB?
Mac Address Bypass (MAB) is a method of authenticating devices based on their MAC Address, this is a common method of authenticating devices on the network that don’t support 802.1x. Many NAC solutions such as Cisco ISE provide a REST API to allow for MAB / Static Group Assignments to be automated.
The Idea, why use iPXE for NAC Enabled Networks?
PXE Booting with NAC enabled ports can be a challenge as they will need access to the network to download the boot file, but if the port is blocked until authenticated the computer will not be able to boot.
For a commercial solution: 2 Pint Software - Details on iPXE 802.1x Integration
Essentially we can put the PXE Server and Unauthorised Devices on a separate localised VLAN only allowing for PXE, authenticate the device with a pin or password and use MAB to allow it to connect to the Imaging Infrastructure such as AD and SCCM after the device has been imaged and has joined the domain it will have an AD Certificate to connect normally.
Investigating with WireShark
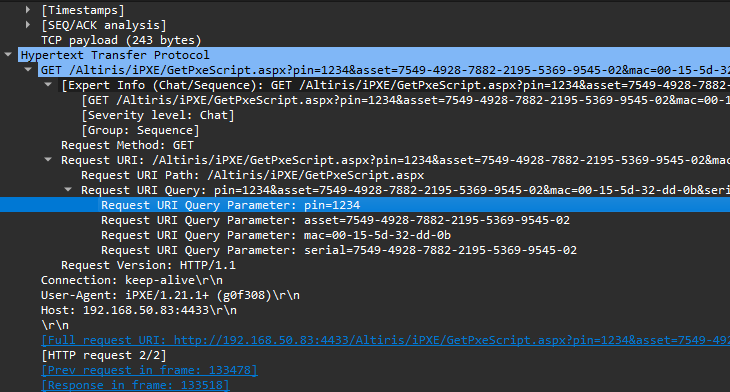
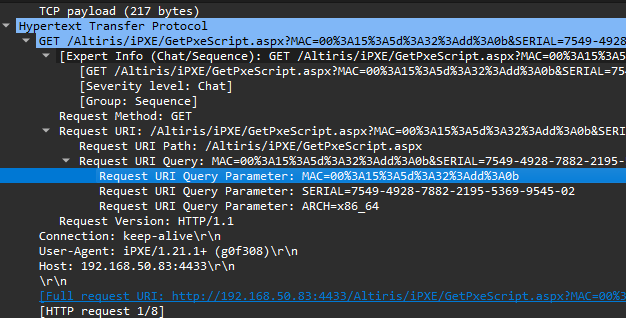
Initial HTTP Request from Broadcom’s iPXE.efi
So we get a MAC Address and Serial Number from the computer to the PXE Server in the HTTP Request:
To automate this we would likely want to prompt the user for a pin or login as-well to ensure the computer is being imaged by someone who is authorised to do so.
If your version of iPXE supports params you can use those as described in the iPXE Documentation or as this isn’t supported by default just passing it to the get request in the url like so:
1
2
3
4
5
6
#!ipxe
echo -n Please provide a pin:
read pin
chain ${pxeurl}GetPxeScript.aspx?pin=${pin}&asset=${asset}&mac=${net0/mac:hexhyp}&serial=${serial} || shell
Another option is to use the username and password params in the iPXE script to authenticate with the PXE server using basic auth:
1
2
3
4
#!ipxe
login
chain https://${username:uristring}:${password:uristring}@${next-server}/AuthPxe.aspx?asset=${asset}&mac=${net0/mac:hexhyp}&serial=${serial} || shell
Conclusion
Now we know how to send the required iPXE requests with useful data about the endpoint, I’ll be writing a follow-up post on creating a TFTP & Web Server for NAC Authentication or Other Scripting, my working prototype is on Github using Rust so stay tuned!
Contact me on Twitter or email in the footer of the left sidebar if you have any questions or feedback.